What is Access Control?
Fundamentally, access control is a security discipline engineered to regulate entry to facilities, specific zones, digital assets, or sensitive data. These systems operate on pre-configured policies to ensure only authorized individuals or entities are granted access, thereby safeguarding personnel, property, and confidential information. This systematic granting or denial of entry is crucial for maintaining security and operational integrity.

Beyond Doors: Physical and Data Protection
While commonly associated with physical entry points like doors and gates, the scope of access control is significantly more comprehensive. An access control system is fundamentally categorized into two main domains:
Physical Access Control
This refers to the systems that manage and restrict entry to physical spaces. Examples include turnstiles in a corporate lobby, boom gates at a secure parking facility, or the controlled doors of a data center. These systems utilize credentials such as key cards, fobs, or biometric data to authenticate identity and authorize passage. The primary objective is to prohibit unauthorized entry into secure areas, thereby protecting valuable assets, equipment, and personnel.
Logical Access Control
Equally vital in the current digital landscape is logical access control. This domain focuses on securing digital assets, including networks, databases, applications, and confidential information. Logical access systems employ methods such as passwords, multi-factor authentication, Virtual Private Networks (VPNs), and firewalls to ensure that only authorized users can access specific digital resources. In South Africa, where organizations face persistent cyber threats, a robust logical access control system is an indispensable component of data protection and intellectual property security.
In integrated ecosystems where physical and digital security converge, both types of access control operate in tandem to create a unified security framework.
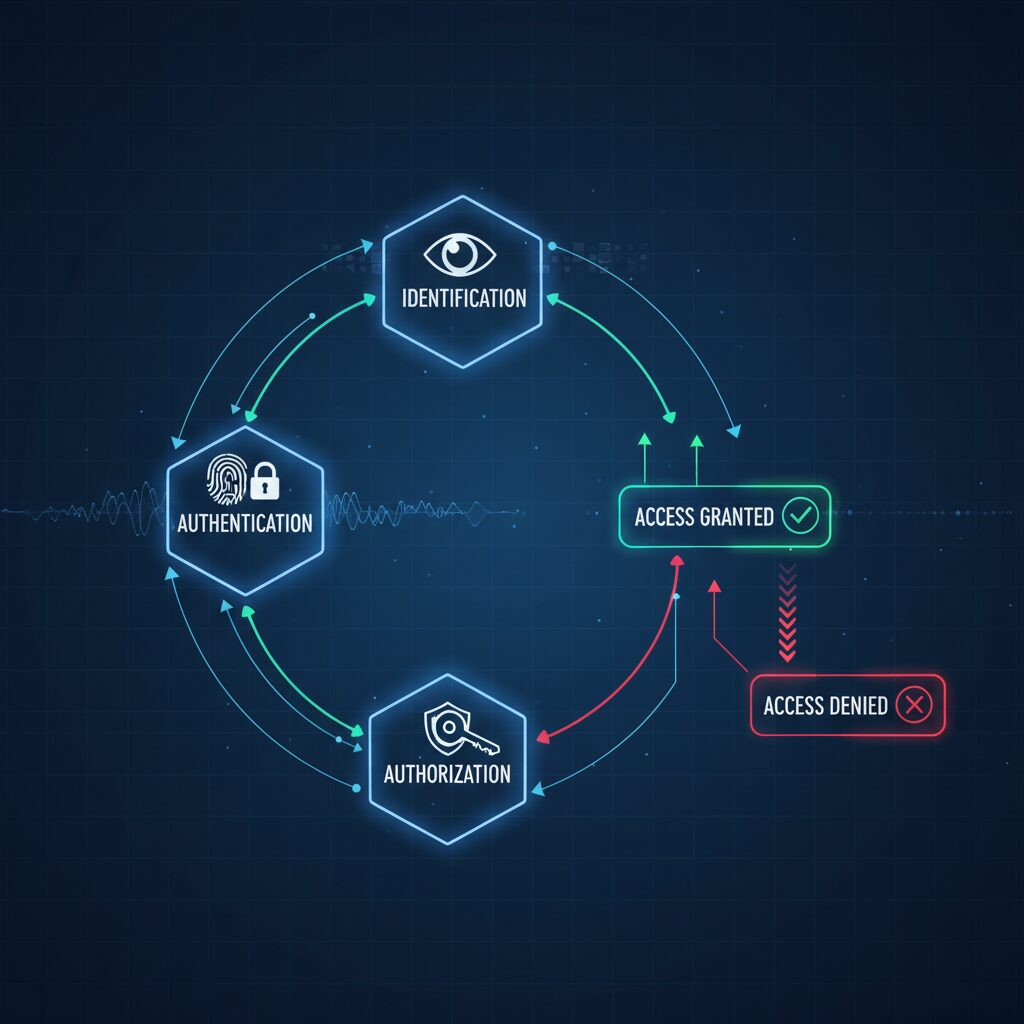
How Access Control Systems Work: The Core Operational Workflow
The core operational workflow for any access control system remains consistent, following a structured process:
- Identification: The system identifies the individual or entity requesting access via a presented credential, such as a physical card, username, or biometric scan.
- Authentication: The system verifies the presented identity. This step proves the individual is who they claim to be, typically through a secondary factor like a PIN, password, or biometric match.
- Authorization: Upon successful authentication, the system cross-references the user’s identity against pre-configured policies and permissions to determine what resources or areas they are permitted to access.
- Access Granted/Denied: Based on the authorization level, the access control system either grants or denies access.

Key Components of an Access Control System
A complete access control system comprises several integral, interconnected components:
- Credentials: The specific data or physical objects used for identification and authentication, such as access cards, key fobs, mobile credentials, or biometric templates.
- Readers/Scanners: These include card readers, facial recognition cameras, and biometric sensors. If you are planning to upgrade your access control system and want to understand the specific mechanics of biometric hardware, we recommend reading our comprehensive breakdown: Fingerprint Scanner: The Ultimate Technical Guide for Business Security.
- Controllers: The central processing units of the system. They process information from readers and execute access decisions based on programmed security policies.
- Locking Hardware: For physical access control, this includes electronic locks, magnetic locks, and electromechanical turnstiles.
- Software: A centralized software platform empowers administrators to manage the entire system, configure user permissions, monitor real-time activity, and generate comprehensive audit reports.
- Barriers: Physical obstacles such as doors, gates, and turnstiles that are controlled by the system to enforce access decisions.
Card-Based vs. Biometric Access
For physical access control, two primary methods prevail: card-based systems and biometric systems. Each offers unique benefits and considerations, and the optimal choice depends on an organization’s specific security requirements and operational context.
Card-Based Access Systems
Card-based systems utilize physical credentials, typically enabled with RFID (Radio-Frequency Identification) or NFC (Near Field Communication) technology, which are presented to a reader to grant access. These can include key fobs or smart cards and are often paired with a PIN to create a multi-factor authentication process.
- Mechanism: A user presents their card to a reader, which transmits the card’s unique identifier to the controller for verification against the system’s database.
- Advantages:
- High Throughput: Ideal for high-traffic environments like corporate offices or public transport systems.
- Cost-Efficient: Generally present a lower initial implementation cost compared to biometric systems.
- User Convenience: Offers touchless access, which enhances hygiene and ease of use.
- Scalability: Enables efficient issuance and revocation of credentials for a large user base.
- Disadvantages:
- Security Risk from Loss or Theft: Credentials can be lost, stolen, or shared, creating a security vulnerability.
- Reduced Security Level: Without a secondary authentication factor, security relies solely on possession of the credential.
- Susceptibility to Damage: Physical cards can be damaged, rendering them inoperable.
- Use Cases: Commonly implemented in hotels, parking garages, general office buildings, and universities throughout South Africa.
Biometric Access Systems
Biometric systems leverage an individual’s unique biological traits for identification and authentication. Common modalities include fingerprint scanning, facial recognition, iris scanning, and voice recognition.
- Mechanism: A user presents their unique biological characteristic to a scanner. The scanner converts this trait into a digital template for comparison against a securely stored database.
- Advantages:
- Superior Security: Biometric data is inherently unique and exceptionally difficult to forge, providing the highest level of identity assurance.
- Credential-Free Operation: Eliminates the need for physical cards or keys that can be carried, lost, or forgotten.
- Enhanced Audit Trails: Provides an indisputable audit trail of user access events.
- Disadvantages:
- Data Privacy Considerations: The collection and storage of biometric data require strict adherence to privacy regulations.
- Increased Implementation Cost: Implementation can be more costly due to specialized hardware and software requirements.
- Potential for Authentication Errors: Environmental factors or issues with the biometric data itself can, in rare cases, lead to false rejections or acceptances.
- Maintenance: Biometric sensors may require periodic cleaning and calibration to ensure optimal performance.
- Use Cases: Frequently deployed in high-security environments such as government facilities, data centers, financial institutions, and laboratories where maximum security is non-negotiable.But this brings up a common question:How much should you actually pay for this level of security?
If you are planning to upgrade your access control system, you need to be careful of “surprise” fees that many vendors don’t mention upfront. We broke down exactly what you should expect to pay in our guide to budgeting for access control: Access Control System Price: Avoid Hidden Costs in SA.
Modern access control trends show a clear convergence of card-based and biometric systems, often integrated with mobile credentials and cloud-based management platforms to create flexible, highly secure, and efficient solutions.
The Future of Access Control
The access control landscape is continuously evolving. The industry is shifting towards more intelligent, integrated access control systems that seamlessly connect with other building management systems (BMS). Mobile credentials, which leverage smartphones as secure access tokens, are becoming increasingly prevalent due to their convenience and robust security features. Cloud-based access control platforms deliver enhanced scalability, remote management capabilities, and reduced on-premise infrastructure costs, making advanced security solutions accessible to small and medium-sized organizations in South Africa. Furthermore, artificial intelligence and machine learning are beginning to play a significant role in enhancing threat detection and predictive security analytics.
Now It’s Your Turn
There you have it: our definitive guide to securing your assets.
We have covered how modern access control systems serve as comprehensive ecosystems, protecting everything from your physical doors to your digital data.
Whether you are evaluating logical access control protocols or deciding between biometrics and key cards, the goal remains the same. You need a solution that ensures business continuity and operational confidence in an increasingly complex world.
Now, we’d like to hear from you.
Which feature of a modern access control system are you looking to implement first?
Are you ready to switch to mobile credentials, or are you sticking with card-based security?
Let us know by leaving a quick comment below.







